AI vs. Endpoint Attacks: What Security Leaders Must Know to Stay Ahead
In the modern digital age, cybersecurity threats are evolving rapidly. As a result, businesses face new challenges in safeguarding their networks and systems. Two primary concerns for security leaders are AI-driven attacks and endpoint threats. Both have the potential to wreak havoc on any organization. It is essential to understand these threats and how to stay ahead in the security game.
Understanding AI-Driven Attacks
AI-driven attacks are becoming more sophisticated, utilizing machine learning (ML) and artificial intelligence to bypass traditional security defenses. These attacks can analyze data quickly and adapt to security systems, making them more difficult to detect. Security leaders must be proactive in understanding these threats to prevent devastating breaches.
One of the biggest challenges is the AI’s ability to mimic legitimate user behavior. This ability allows cybercriminals to carry out advanced phishing attacks and other social engineering tactics. Furthermore, AI can generate malware code that adapts dynamically to avoid detection.
To combat AI-driven attacks, security leaders should integrate AI-powered security solutions that can detect anomalies and predict new attack patterns. Machine learning can enhance the capability of security systems to identify unusual activity and respond swiftly to prevent an attack. Additionally, AI-based threat detection solutions are increasingly critical for staying ahead of these attacks.
Endpoint Attacks: A Growing Concern
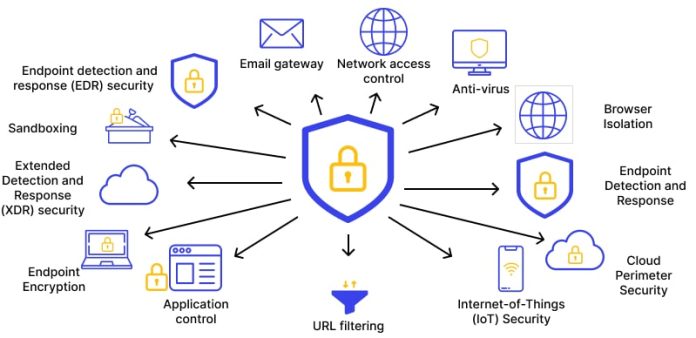
Endpoints such as laptops, smartphones, and IoT devices serve as prime targets for cybercriminals. These devices often hold sensitive information and can be easily exploited if not properly secured. Endpoint attacks typically involve malware, ransomware, or unauthorized access.
It is critical for businesses to implement a comprehensive endpoint security strategy. A zero-trust security model can significantly reduce the risk of an endpoint breach by limiting access to only verified users and devices. Learn more about the zero-trust model and how it can protect your endpoints.
In addition, ensuring that all devices are equipped with updated antivirus software and regularly patched systems is vital. Security leaders should train employees on identifying potential threats and exercising caution when connecting to networks. You can read more on effective endpoint protection strategies.
How AI Enhances Endpoint Protection
AI can play a crucial role in protecting endpoints. By using machine learning algorithms, AI-powered endpoint protection tools can automatically detect suspicious activity and respond instantly. These tools can continuously monitor and adapt to evolving threats.
For example, AI can analyze user behavior patterns to identify anomalies. If an endpoint behaves in an unusual way, such as attempting to connect to unauthorized networks, AI can raise an alert and block further activity. Endpoint detection and response (EDR) technologies powered by AI are becoming more critical in detecting and mitigating threats in real-time.
Additionally, AI-enabled systems can ensure faster threat detection and remediation, reducing the time it takes to address a security breach. This speed is essential in preventing damage and limiting data loss. AI in endpoint security is not only reactive but also proactive in identifying potential threats before they escalate.
Why Integrating AI in Cybersecurity is Crucial
The integration of AI into cybersecurity frameworks provides organizations with a dynamic defense mechanism. With predictive capabilities, AI helps security teams stay one step ahead of cybercriminals. It can identify trends and anticipate emerging threats, allowing organizations to act before a breach occurs.
By leveraging AI, security leaders can automate routine security tasks, freeing up resources to focus on more complex threats. Moreover, AI helps in real-time analysis of vast amounts of data, enabling faster detection of potential vulnerabilities in the system. Learn how AI-powered security tools are reshaping how organizations combat cyber threats.
Best Practices to Stay Ahead of Endpoint Attacks
To stay ahead of endpoint attacks, security leaders must adopt a multi-layered defense strategy. This strategy includes implementing AI-based security tools, using encryption to protect sensitive data, and ensuring constant software updates. Regular employee training on cybersecurity best practices is also vital. Endpoint protection strategies help prevent the exploitation of vulnerable devices.
Additionally, security leaders should monitor endpoint activity continuously. Utilizing cloud-based security solutions helps protect remote devices and ensures access control even in decentralized environments. Cloud-based security solutions can also integrate AI to identify threats from anywhere, at any time.
Conclusion: Protecting Your Organization from AI and Endpoint Attacks
In conclusion, both AI-driven attacks and endpoint threats present significant risks to organizations. Security leaders must continuously adapt to these evolving challenges by incorporating AI technology, implementing strong endpoint protection measures, and fostering a cybersecurity-aware culture. By doing so, they can stay ahead of potential threats and safeguard their organization’s critical assets.
for the actual source of the news visit:
AI vs. endpoint attacks: What security leaders must know to stay ahead
For more details of Endpoint Security: